Tutorial: Switch only operation with Dell Enterprise SONiC in GNS3
This tutorial will walk you through the steps needed to build up a topology in GNS3 and use MetalSoft to control the fabric.
Prerequisites
Section titled “Prerequisites”For this tutorial you will need a working CLI setup.
The tutorial doesn’t use ZTP due to complications with L2 setups on laptops thus the switch needs to be already configured with:
- Management interface
In addition, if EVPN is used the following must be configured:
- A VTEP interface
- A ASN
- A Loopback interface
And provided below to the switch as configuration.
Download and install the Site Controller OVA
Section titled “Download and install the Site Controller OVA”Site Controller OVA: 4 cores, 8GB RAM
- click import in VMWare fusion
- Click Finish
Wait until the VM booted up and login to the VM
- Username:
root - Password:
MetalsoftR0cks@$@$
DHCP is enabled by default. If necessary edit the netplan /etc/netplan/00-installer-config.yaml file (OS is Ubuntu) to suit your needs.
Configure the Site Controller
Section titled “Configure the Site Controller”-
create a file such as
local-dc.yaml. Most of the settings can be left as they are. Modify just theBSIMachinesSubnetIPv4CIDR,BSIVRRPListenIPv4andBSIMachineListenIPv4Listto match your Site Controller’s IP.BSIMachinesSubnetIPv4CIDR: 192.168.1.11/24BSIVRRPListenIPv4: 192.168.1.11BSIMachineListenIPv4List:- 192.168.1.11BSIExternallyVisibleIPv4: 209.43.59.203repoURLRoot: http://<repo>repoURLRootQuarantineNetwork: http://<repo>SANRoutedSubnet: 100.96.0.0/16NTPServers:- 45.55.58.103DNSServers:- 1.1.1.1- 8.8.8.8KMS: 84.40.58.70:1688TFTPServerWANVRRPListenIPv4: 10.73.252.10dataLakeEnabled: falselatitude: 41.8426112longitude: 87.6695329serverRegisterUsingGeneratedIPMICredentialsEnabled: falseserverRegisterUsingProvidedIPMICredentialsEnabled: trueswitchProvisioner:LAGRanges:- 5-25LANVLANRange: 400-450MLAGRanges:- 26-27SANVLANRange: 300-399WANVLANRange: 100-199allocateDefaultLANVLAN: trueallocateDefaultSANVLAN: falseallocateDefaultWANVLAN: trueleafSwitchesHaveMLAGPairs: falsepreventCleanupForVLANs:- 301- 1602preventCleanupForVLANsFromExternalConnectionUplinks:- 301- 1602preventUsageOfVLANs:- 301- 1602quarantineVLANID: 5storageHasSeparateFabric: falsetype: EVPNVXLANL2ProvisionerzeroTouchRegistrationEnabled: trueenableTenantAccessToIPMI: falseallowVLANOverrides: trueallowNetworkProfiles: trueenableServerRegistrationStartedByInBandDHCP: falseextraInternalIPsPerSubnet: 0extraInternalIPsPerSANSubnet: 0serverRAIDConfigurationEnabled: truewebProxy:ip: 10.73.252.10port: 3128isKubernetesDeployment: falseallowInstanceArrayFirmwarePolicies: falseprovisionUsingTheQuarantineNetwork: trueenableDHCPRelaySecurityForQuarantineNetwork: falseenableDHCPRelaySecurityForClientNetworks: falseenableDHCPBMCMACAddressWhitelist: truedhcpBMCMACAddressWhitelist:- 6C:2B:59:7C:0F:D3- CC:48:3A:09:EB:97defaultServerCleanupPolicyID: 0defaultDeploymentMechanism: virtual_mediadefaultCleanupAndRegistrationMechanism: bmcNFSServer: 172.18.38.38Option82ToIPMapping: {}flags: "" -
Run
site create:% metalcloud-cli site create --config local-dc.yaml --format yaml --id local-dc-1 --title "Local DC 1" -
Get the site auth URL
metalcloud-cli site get --id local-dc-1 --return-config-urlhttps://us05.metalsoft.io/api/url?rqi=br._mJHHCUMW7I1kwwNjYNh3HWcpwwvfwVo7RKlQVLGn9PbElV_hxvDq4CE79bFrw70MYmANJmtorHvwupXZG2OWTNm5Eszg84QVq5z8Cm19qU&v=YojW5IXpEARy6VA4_EUHNw&filename=site.json&site_name=local-dc-1 -
SSH into the Site Controller using the following username and pass:
- Username:
metalsoft - Password:
MetalsoftR0cks@$@$
ssh -l metalsoft <IP> - Username:
-
Check if the Site Controller agents are now connected
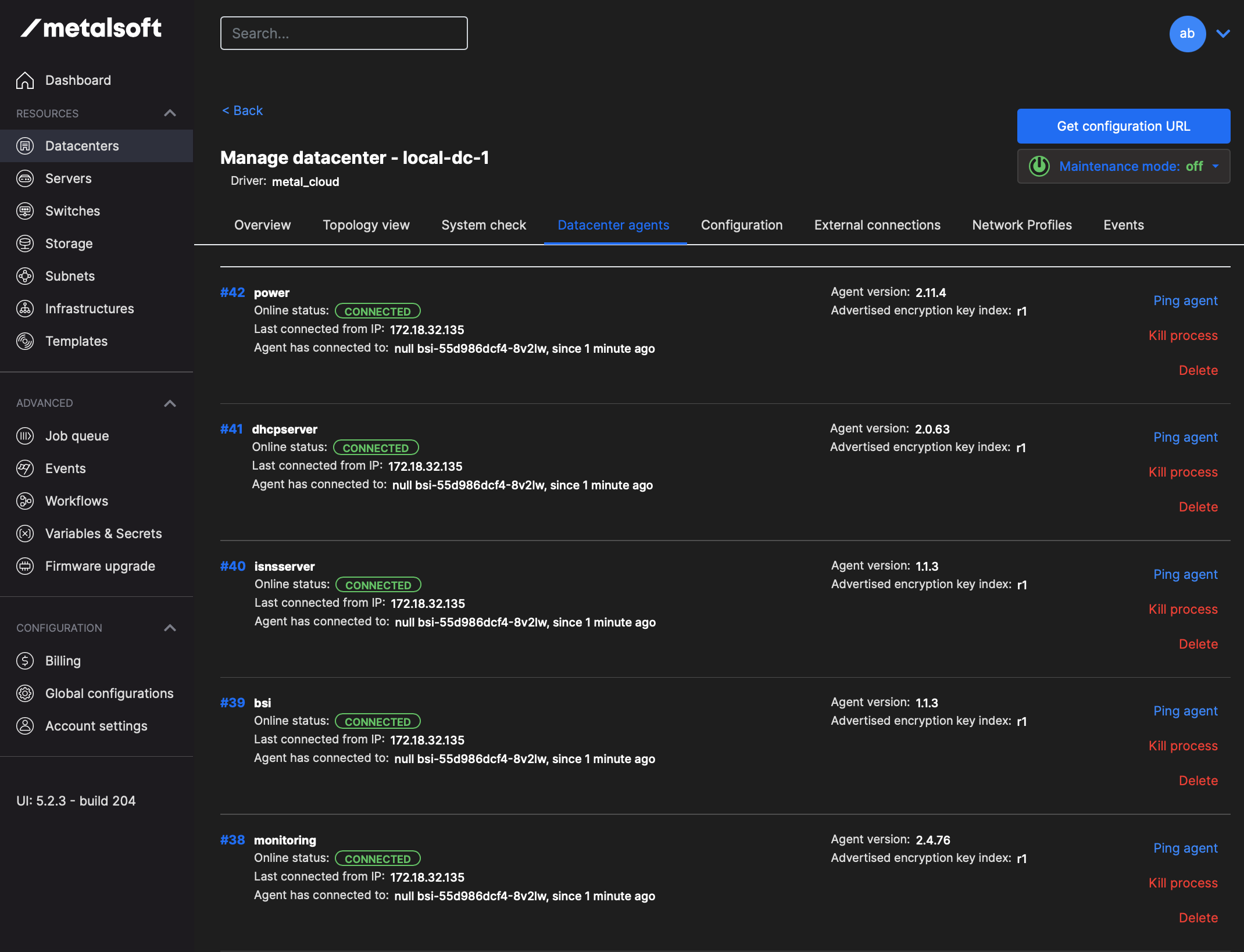
Import MetalSoft VM into GNS3
Section titled “Import MetalSoft VM into GNS3”This example uses GNS3 version 2.2.33.1 but should apply to all GNS3 versions
-
Create a GNS3 project

-
Import Site Controller appliance by following these steps:
-
Go to on File > New Template > Manually create a new template
-
VMWare Fusion > New Select the
Site ControllerVM from the list:
-
Click finish
-
Build the topology in GNS3
Section titled “Build the topology in GNS3”- Add the Site Controller vm, a switch and two hosts.
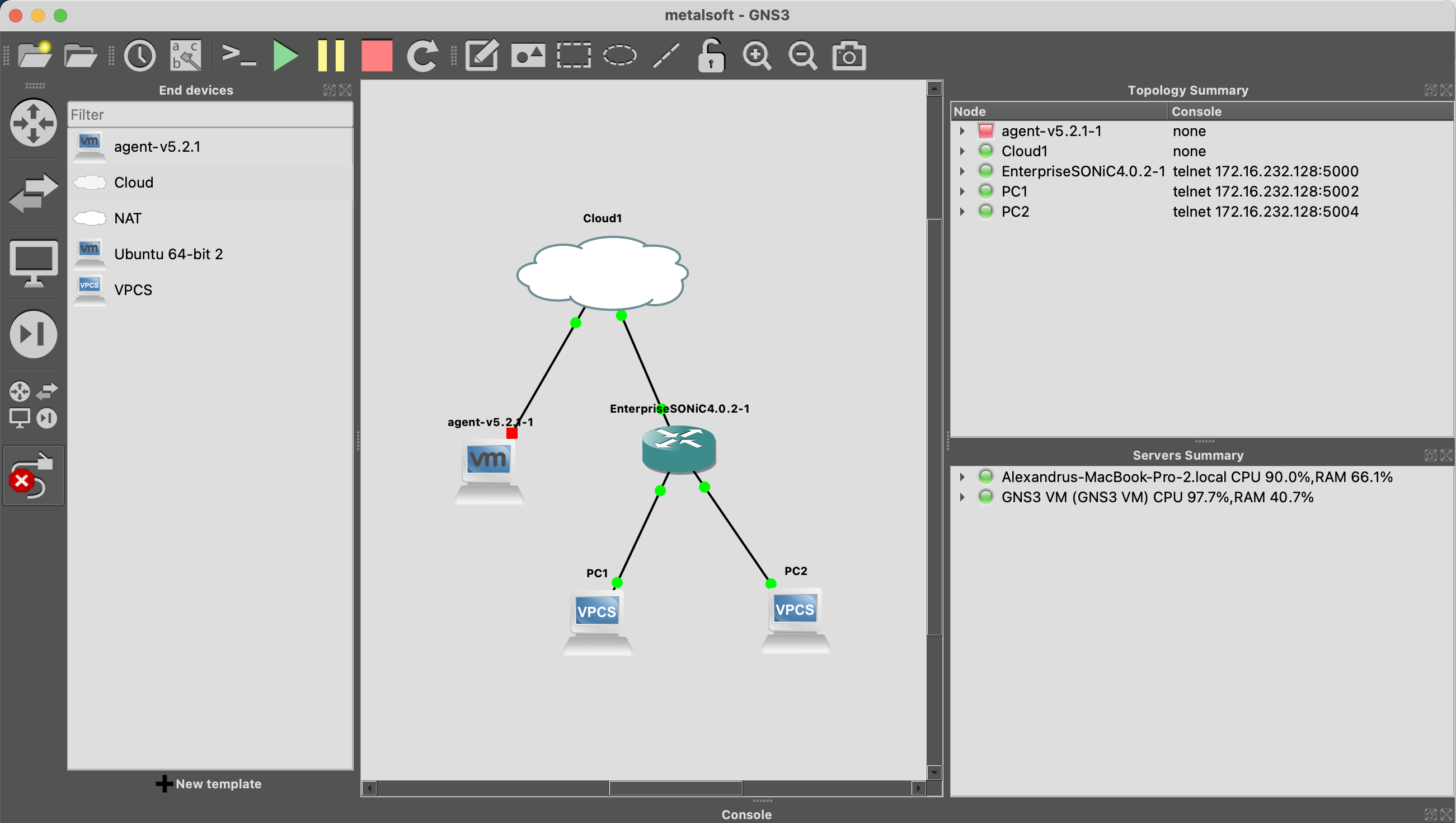
Note that connecting the Site Controller to the “Cloud” is not strictly required. If the virtual machine is connected to the host’s NAT the effect would be the same. However zero touch provisioning might not work.
Register the switch in MetalSoft using the CLI
Section titled “Register the switch in MetalSoft using the CLI”-
Create a file called
sw.yaml. Most of the settings can be left to the defaults, you can alter just themanagementAddressfield and themanagementPasswordfield. Note also the VTEP, ASN and Loopback fields that need to be set if EVPN is used.identifierString: sonic01siteName: local-dc-1provisionerType: evpnvxlanl2provisionerPosition: leafdriver: sonic_enterprisemanagementUsername: adminmanagementPassword: YourPaSsWoRdmanagementAddress: 192.168.1.25managementAddressMask: 255.255.255.248managementAddressGateway: 192.168.255.1managementMACAddress: 8c:04:ba:ea:60:c0primaryWANIPv4SubnetPool: 10.0.0.1primaryWANIPv4SubnetPrefixSize: 24primarySANSubnetPrefixSize: 24quarantineSubnetStart: 192.168.67.1quarantineSubnetEnd: 192.168.67.254quarantineSubnetPrefixSize: 24quarantineSubnetGateway: 192.168.67.1tags:- tagrequiresOSInstall: falseisBorderDevice: falseisStorageSwitch: falsenetworkTypesAllowed:- wan- san- lan- quarantineLoopbackAddress: 10.0.90.3VTEPAddress: 10.0.91.2ASN: 65102 -
Run
switch create
./metalcloud-cli switch create --raw-config sw.yaml --format yamlThis command might take up to 30 seconds.
The switch should now be in active state:
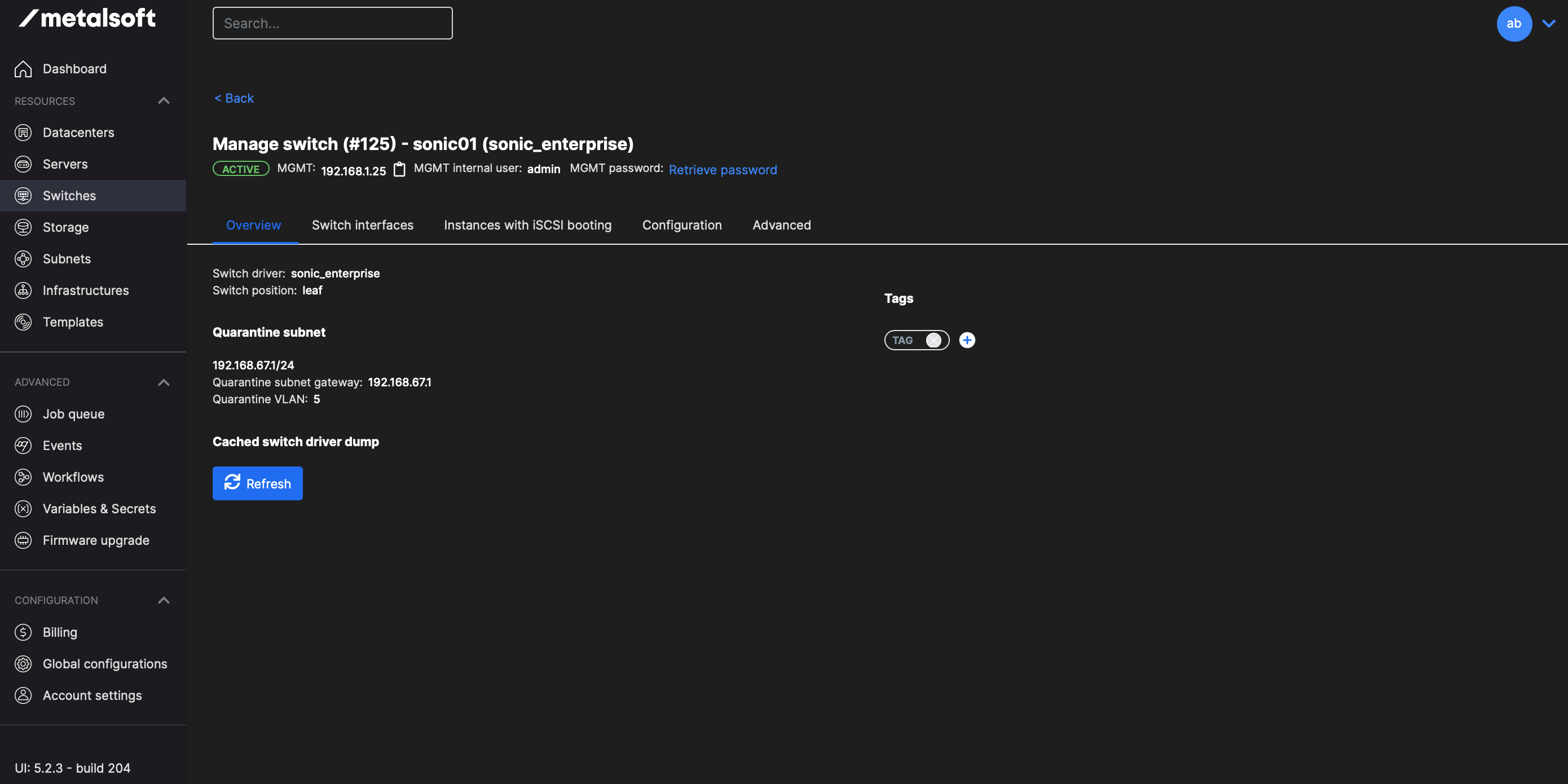
Create a network profile
Section titled “Create a network profile”This is not strictly required but if you decided not to use EVPN this is how you would disable it:
-
If you are reusing an existing site rather than creating a new one using the configuration above, make sure to enable network profiles and automatic VLAN allocation by navigating to the Fabrics > select fabric > Configuration and: Add a default VLAN
-
Create a file called
network-profile.yaml:label: internet01site: local-site-1networkType: wanvlans:- vlanID: null #auto-allocatedportMode: nativeprovisionSubnetGateways: false # do not provision a gateway SVIprovisionVXLAN: false # set this to false to disable EVPNextConnectionIDs: [] -
Create the network profile
metalcloud-cli network-profile create --raw-config ~/Desktop/network-profile1.yaml --site local-dc-1 --format yaml
Adding the GNS3 PCs as un-managed servers
Section titled “Adding the GNS3 PCs as un-managed servers”We will now add the two PCs as un-managed servers. Note: By default MetalSoft does not allow servers with a single interface to be added. Go to Global Configuration > Advanced and enable “Allow servers with one interface” option then click save.
-
If you do not already have one, create a new “unmanaged” server type: Navigate to Servers > Server types tab > Add server type. a. Provide a name and a random SKU b. Check the “Unmanaged” checkbox at the bottom of the form.
-
Create a file called
servers.yamlsite: local-site-1serialNumber: PC1serverType: M.15.15.1interfaces:- mac: 00:B0:D0:63:C2:26switch: sonic01switchInterface: Ethernet1---site: local-dc-1serialNumber: PC2serverType: M.15.15.1interfaces:- mac: 00:B0:D0:63:C2:26switch: sonic01switchInterface: Ethernet2 -
Import the servers
metalcloud-cli server import-batch --file servers.yaml --format yaml
The servers should now show up in the Servers section:
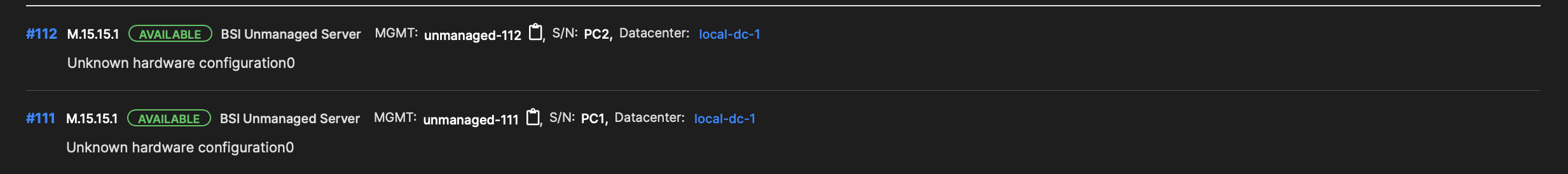
We are now ready to start deploying network configurations.
Provisioning a network using the self-service interface
Section titled “Provisioning a network using the self-service interface”This is how end-users will be consuming the network profile that you configured. In this case the same user will be performing both the definition of the service and the consumption part, but in a real setting the end-user and the admin will be different. End-users will receive access to their ‘infrastructure’ with the servers already added.
- Access the Infrastructure designer from the upper right corner menu with the user’s initials.
- If a single site exists then the default infrastructure will be created. If not, create an infrastructure in the local site you just created.
- Click “Create your first instance array”
- Select the unmanaged server type used.
- Select one of the servers you just added in the dropdown below.
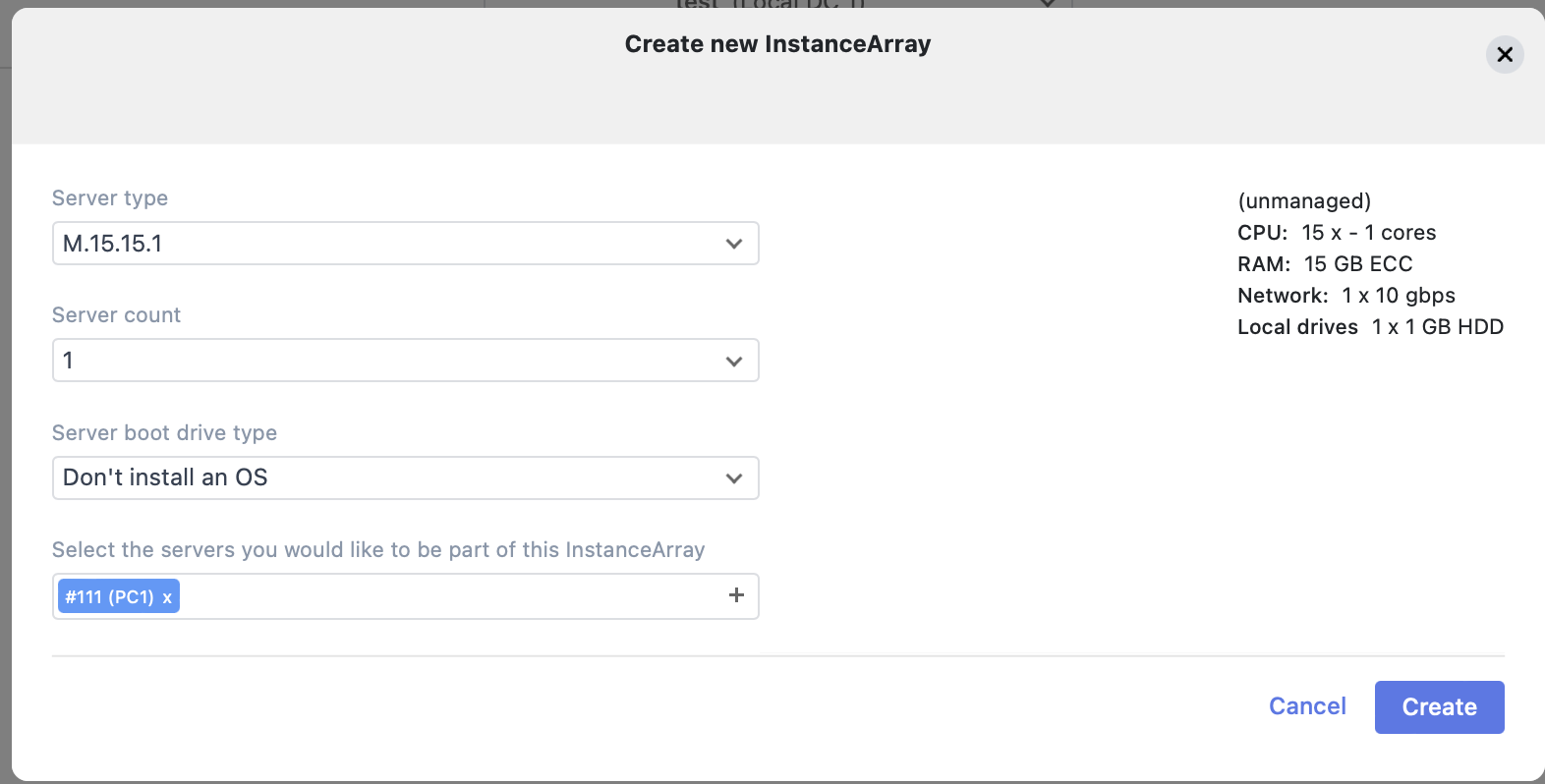
- Select the network profile ‘internet01’. Alternatively use the Advanced tab to select it on both servers.
- Click save.
- Repeat the process for the other server
The two servers are now connected to the default “WAN” network.
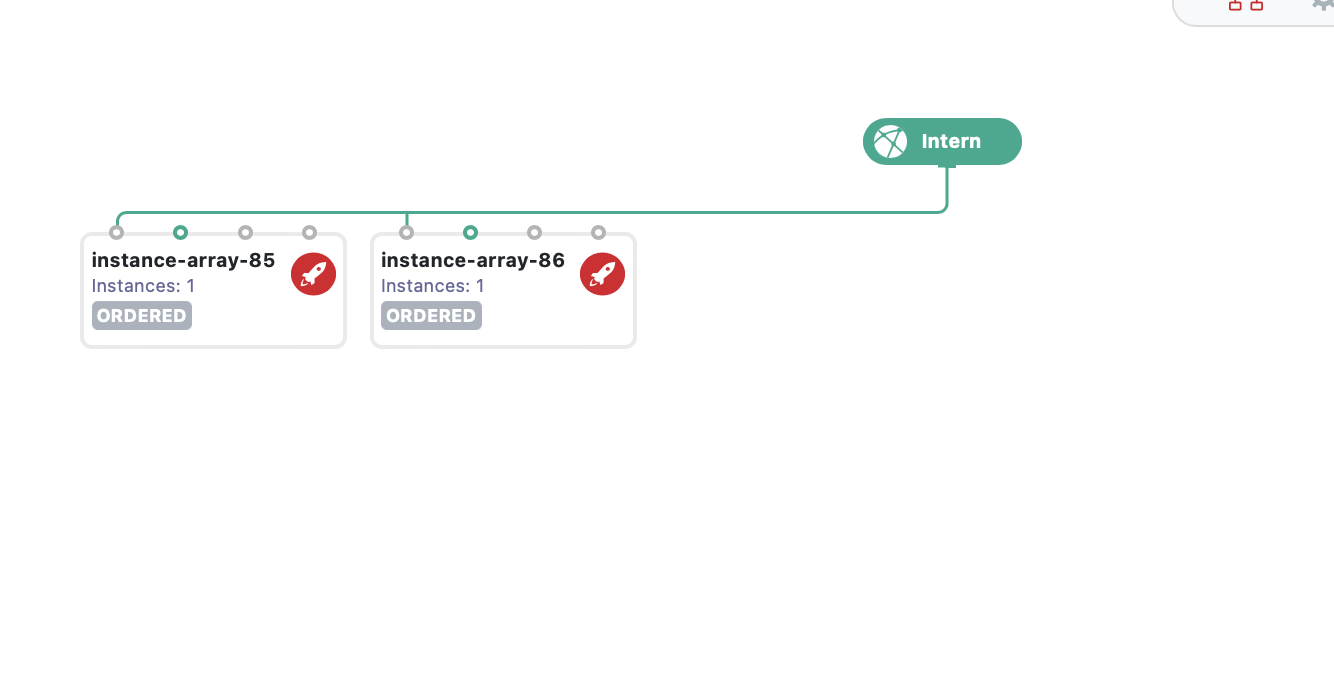
Click the Deploy button on the bottom.
At the end of the deploy both servers will show as ‘Active’.
You have now successfully provisioned a network “as a Service”.
Next steps
Section titled “Next steps”Learn more about networks and network profiles Networking Overview