Getting Started
Welcome to MetalSoft!
Section titled “Welcome to MetalSoft!”The MetalSoft CloudPlex Platform is a powerful Software Defined Datacenter (SDDC) platform, with various modules that can handle many different use cases. Not all modules are used at the same time by all customers. The most common use cases for the MetalSoft platform are the following:
- Full Stack deployment (servers, switches, storage, clusters etc.) In this setup all of MetalSoft functions are used in conjunction with one another.
- Fabric Manager (network only management) In this setup only the network part is used.
- Bare-Metal-as-a-Service (physical compute and storage but with externally managed network) In this setup the clients consume the Bare-Metal-as-a-Service via CI/CD or the client user interface but network provisioning is done outside MetalSoft either coordinated externally or via MetalSoft workflows.
- GPU-as-a-Service (A variation on the Full Stack Deployment or the BMaaS) In this setup the clients consume the Bare-Metal-as-a-Service (BMaaS) and/or VM-as-a-Service (IaaS) via CI/CD but network provisioning is done outside MetalSoft either coordinated externally or via MetalSoft workflows.
- VM as a Service - IaaS (VM cluster deployment and VM management) In this setup the consumption is primarily via VMs rather than Bare Metal nodes. MetalSoft handles cluster provisioning and lifecycle, potentially across multiple hypervisors. The networking part is done via network provisioning (overlay networks are implemented at the switch layer rather than in software).
MetalSoft components
Section titled “MetalSoft components”The MetalSoft CloudPlex Platform is modular and some but not necessarily all modules are used in various use cases depending on requirements and existing automation.
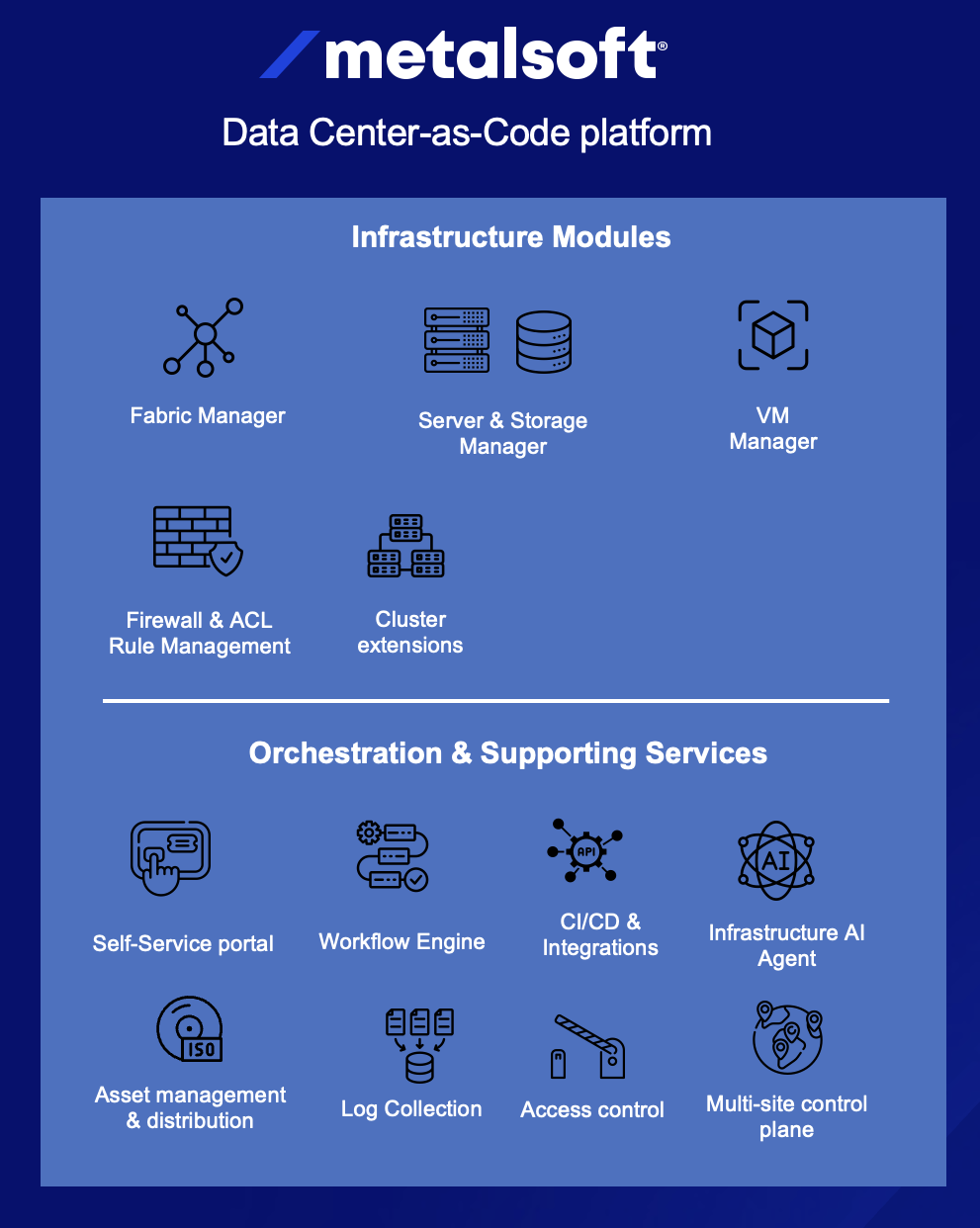
Components used for various use cases
Section titled “Components used for various use cases”| Use case | Fabric Manager | Server & Storage Manager | VM Manager | Cluster Manager |
|---|---|---|---|---|
| Full Stack deployment | yes | yes | yes | yes |
| Fabric Manager | yes | no | no | no |
| Bare Metal-as-a-Service | yes | no | no | no |
| GPU-as-a-Service | yes | yes | yes | no |
| VM-as-a-Service (IaaS) | yes | yes | yes | no |
Where to go from here
Section titled “Where to go from here”Depending on what you are using it for you may find that some materials are more important than others. Nevertheless we recommend starting with the the overall architecture and then moving on to learn about the various aspects related to the respective use case.