Managing network profiles¶
Network profiles are a logical network template for consumers to select when setting up a Private network.
This allows the network admins to prepare the templates that make is easier for users without deep networking understanding to create their private logical networks from the correct template.
Creating a new network profile¶
Network profiles are created at the Fabric level and are used by users. Unless given network_profiles_write permission regular users will not be able to create such profiles given the security risk this might generate but they can use the profiles.
Each network profile can have one or more VLAN entries. These VLAN entries control which VLANs (and in the case of the eVPN provisioner VNIs ) get terminated on the WAN port and how.
To set up a network profile, go to Fabrics, Fabric Name, Network Profiles tab. Click on Add network profile. Add a Name, Chose the Kind between vlan and vxlan. Choose whether the Allocation strategy is auto or manual. Select the Scope of the network profile (Currently only fabric available).
Editing a VLAN Network profile¶
To edit a VLAN Network profile, navigate to network profiles and click on the network profile
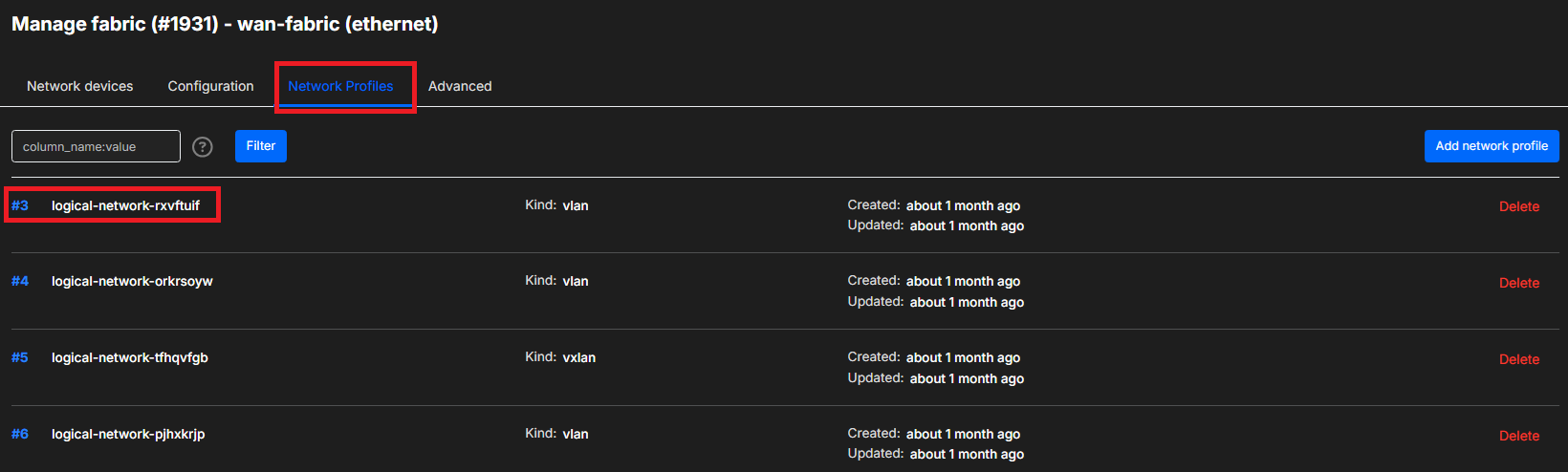
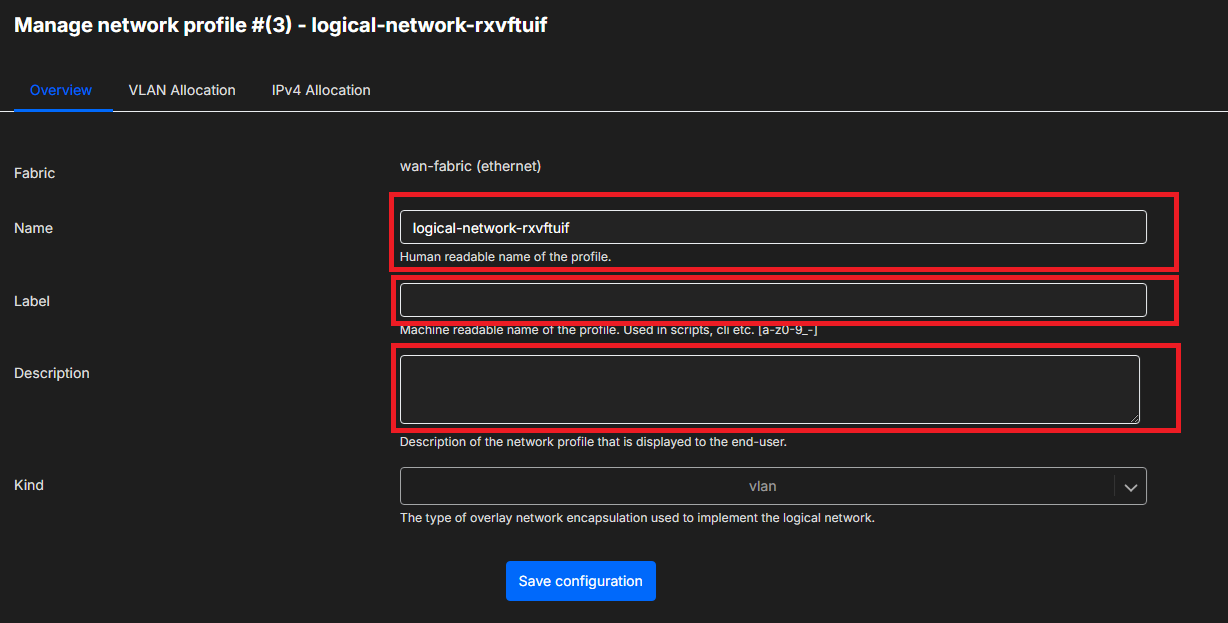
Within the Overview tab, the Name, Label and Description can be changed
Click on the VLAN Allocation tab to changed the Allocation strategy, the Scope and the Granularity level. Changing the Allocation strategy from Automatic to Manual allows the ability to assign a specific VLAN.
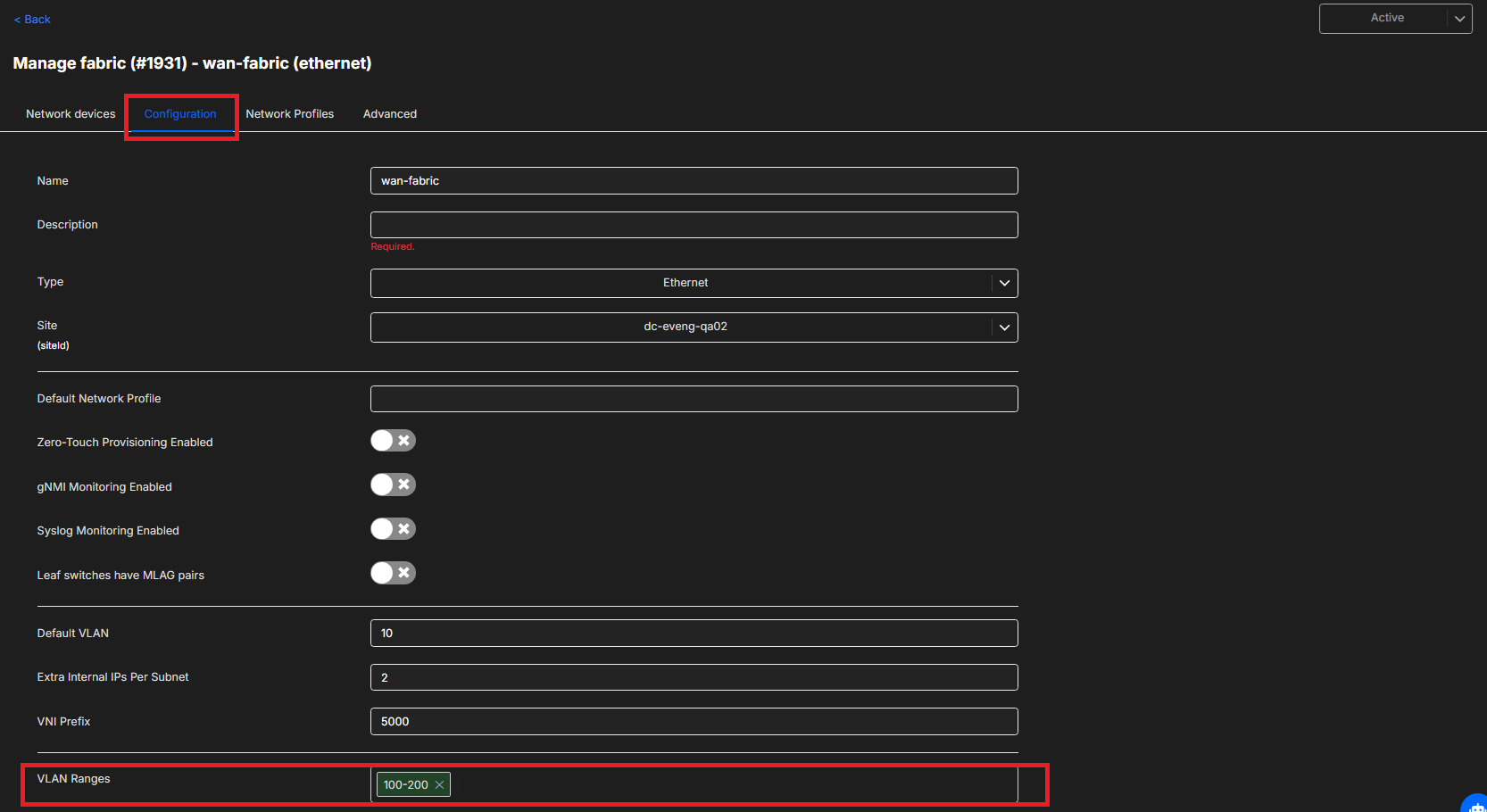
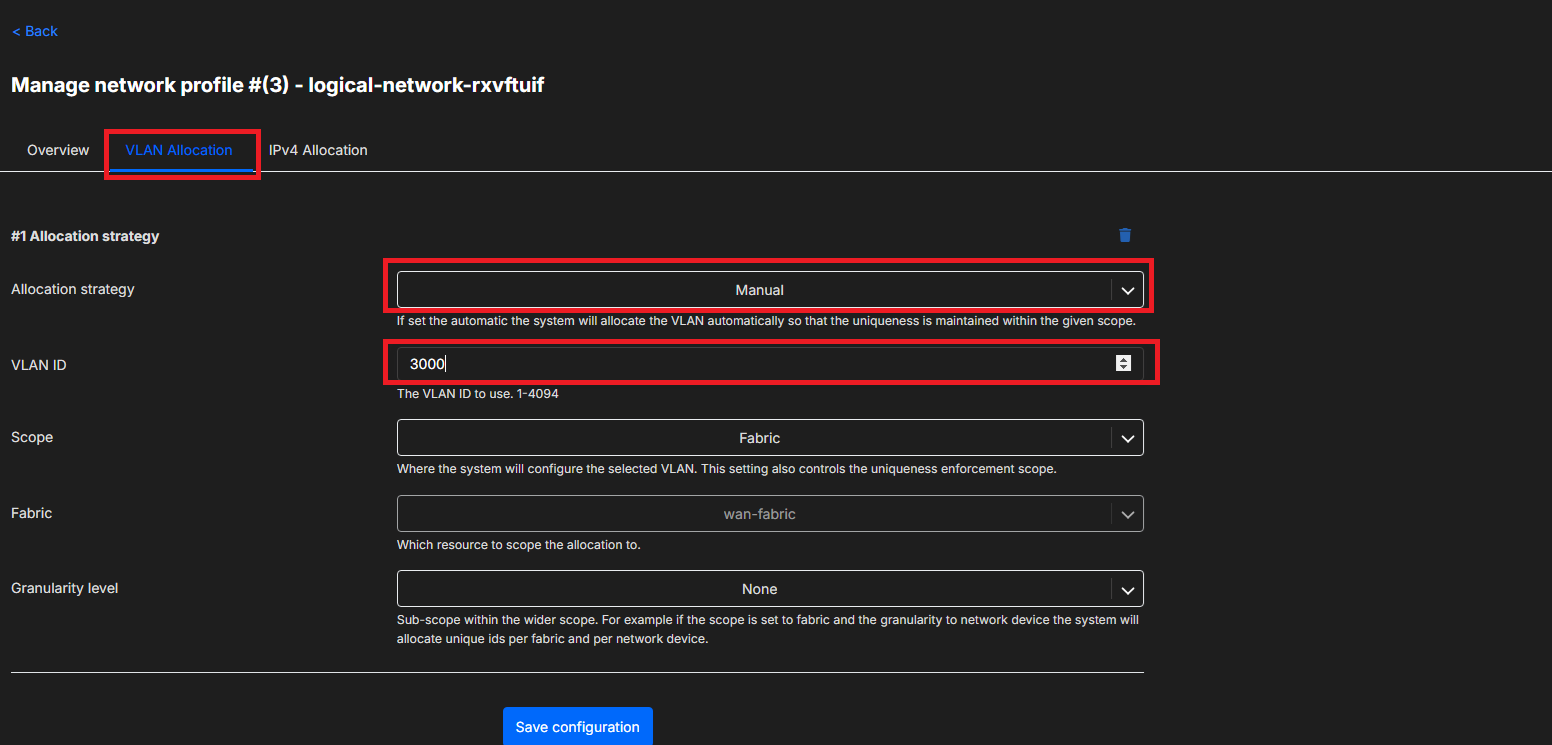 Please ensure this VLAN is not already in the range added to the Fabric that the Network profile is created under (
Please ensure this VLAN is not already in the range added to the Fabric that the Network profile is created under (Fabrics, Fabric Name, Configuration, VLAN Ranges).
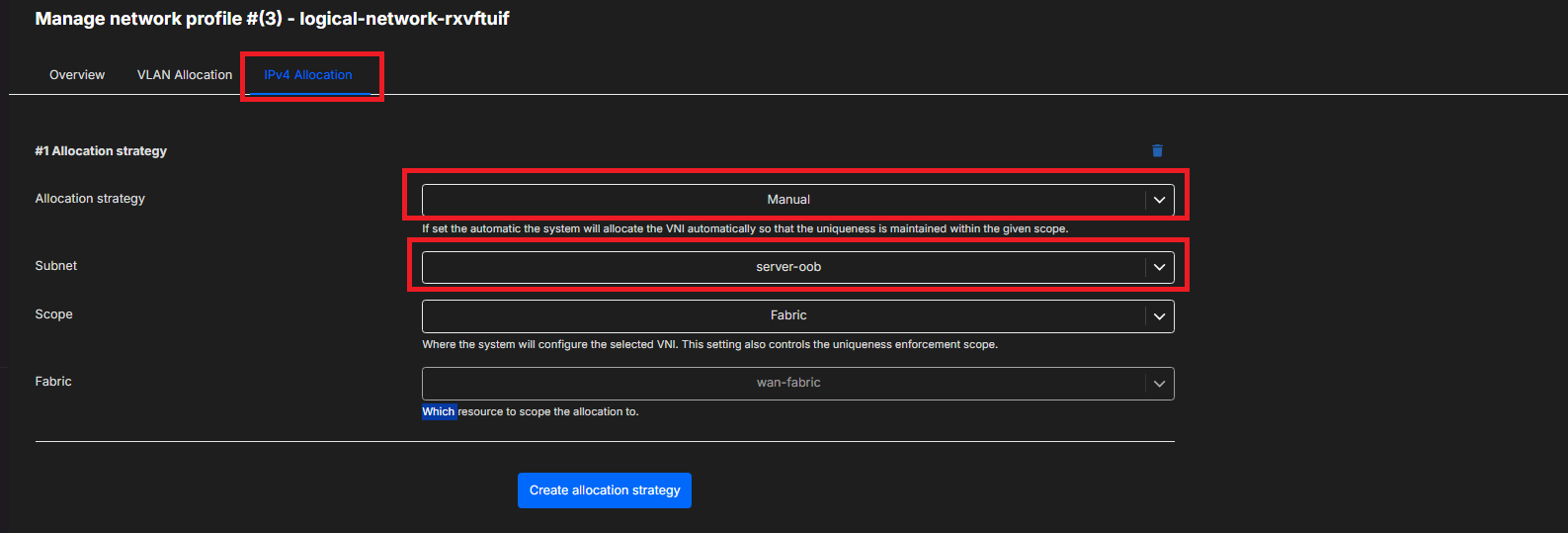
Click on the IPv4 Allocation tab to change the Allocation strategy, the Subnet Pools assigned, the Prefix length and the Scope. Changing the Allocation strategy from Automatic to Manual allows the ability to assign a specific IPv4 subnet.
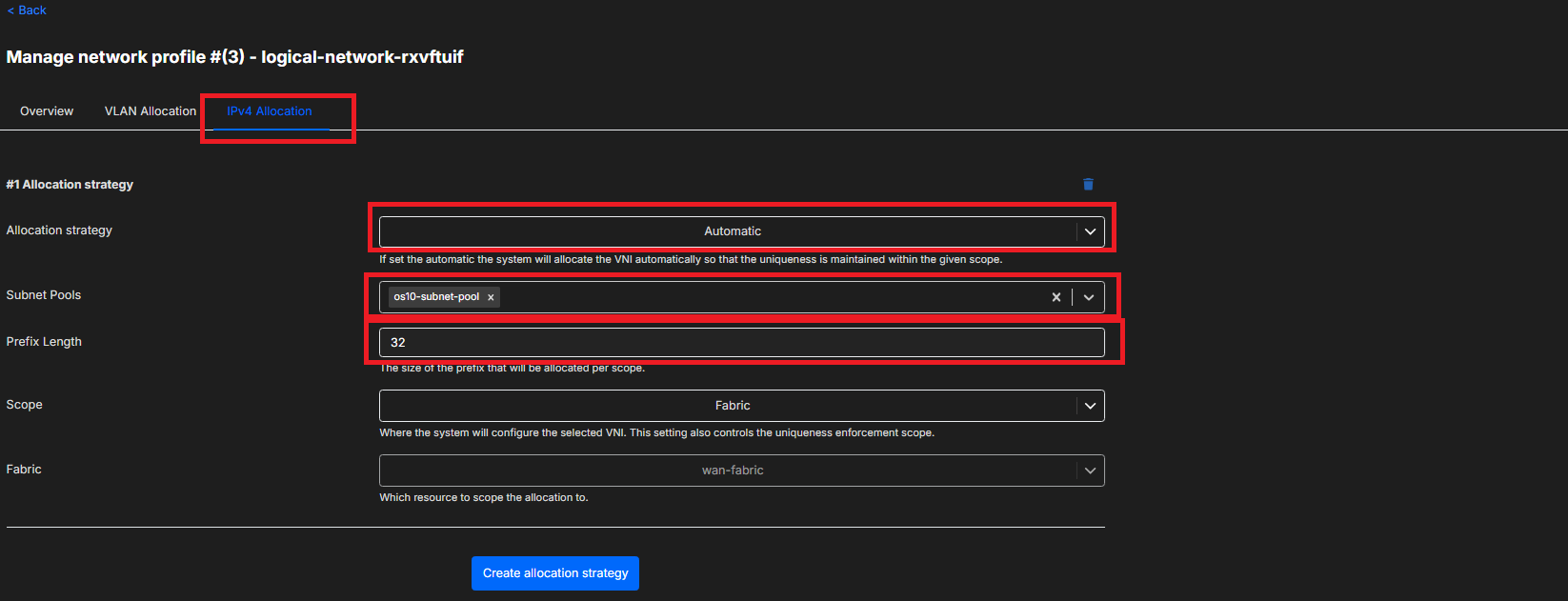
 Changing the Allocation strategy to Automatic allows the ability to assign a specific IPv4 subnet pool and prefix length.
Changing the Allocation strategy to Automatic allows the ability to assign a specific IPv4 subnet pool and prefix length.
Once the network profile is set up as desired, it will be visible in the Infrastructure Designer for the consumer to select when using a Private network.